Whenever we are working on software projects almost always we're handling sensitive data and information such as access keys, API keys, usernames, passwords, and much more. I personally like to utilize Hashicorp's Vault to manage my secrets and sensitive data as well as integrate it with my automation tooling such as Ansible. Let's dive into this tutorial step by step on how to use Ansible and retrieve secrets from Vault to integrate into your automated workflows and playbooks:
Prerequisite Initial Steps
If you do not have Hashicorp Vault set up, follow the link below to set up Vault with Docker.

Once the setup is complete and you created your access token you have to set environment variables on the systems you are going to utilize vault to retrieve secrets and run Ansible playbooks. For this tutorial, we are going to run one Ansible playbook on one of my remote hosts to test our Ansible config and code. Run the following commands below on the remote host to set the env vars:
VAULT_ADDR=vaultADDR >> .bashrc #add your vault ip address here
VAULT_TOKEN=vaultToken >> .bashrc #add vault token here
source .bashrcOnce your vars are set run this command on the remote host to see if your env vars are properly set up - echo $VAULT_ADDR which should print out the value which is your Vault address.
Ansible Playbook Scripts And Config
The next step is to create a directory in your Ansible repo, I am naming the directory vault_example for the purpose of this tutorial. Create the two yaml files below in the directory:
vars.yml
This file will host all your vars and in this case, will be the configuration that utilizes the system variables and establishes a connection to the Vault Server which would enable us to call secrets and add it to our playbook workflow.
---
## vault
vault_data: "{{ lookup('hashi_vault', 'secret=example/data/test token={{ ansible_env.VAULT_TOKEN }} url={{ ansible_env.VAULT_ADDR }}') }}"
example_vault.yml
This example playbook is going to establish a connection to the Vault Server and retrieve the example I created here called example_value and print out the secret.
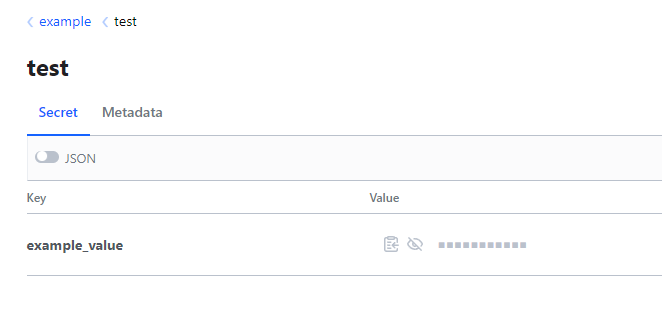
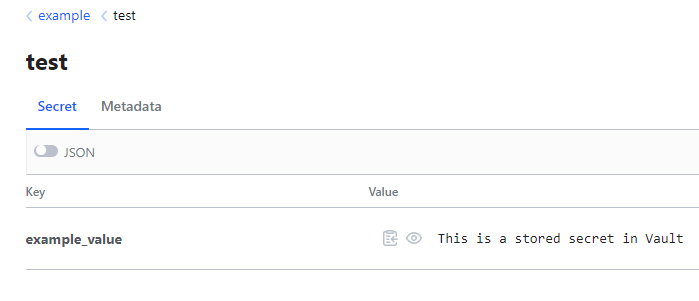
---
- name: Vault data - stored secret example
hosts: dh1
vars_files:
- "vars.yml"
tasks:
- name: Get example secret value from vault server
debug:
msg: "{{ vault_data.example_value }}"
Run the following ansible-playbook command depending on your Ansible setup or config it could be a little bit different - ansible-playbook --key-file ~/.ssh/ansible_rsa -i inventory playbooks/vault_example/example_vault.yml if the playbook workflow succeeds the following output below should display in your CLI terminal.
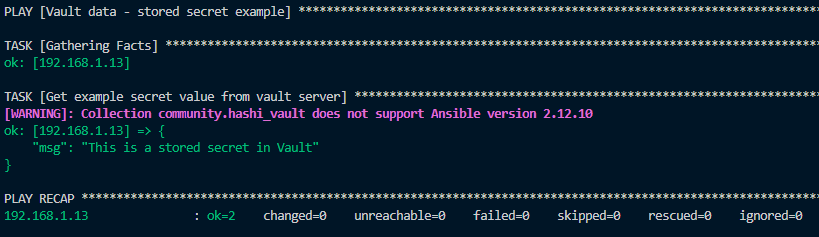
Conclusion
In conclusion, there are many open-source tools that can be integrated to make automated workflows possible and more secure. Hashicorp's Vault Secrets Manager or Server is a very good choice and integrates well with tools like Ansible as showcased in this tutorial but also software like Terraform and much more. If you enjoyed this article consider signing up for our newsletter and don't forget to share it with people that would find it useful. Leave a comment below with a tutorial you would like us to cover.


